Quick Contact Request
Please fill in information below and we will be in touch shortly.
Avoiding the Counterfeit Trap: Electronic Component Counterfeits In An EMS Supply Chain
September 5, 2017 by Philip P. Thurman | News

Allowing electronic component counterfeit contamination into an EMS supply chain is more than just basic root cause and corrective action, it’s a fundamental breach of trust between manufacturers, customers, and all stakeholders. No amount of certifications, zero find audits, or established performance history excellence compensates for the financial damage, reputation loss, and confidence forfeiture due to counterfeit components populated and shipped to a customer. Even more devastating and immeasurable, jeopardizing injury or resulting loss of human life. In a recent Scientific American article, L. Greenemeier (2017) states “The military estimates that up to 15 percent of all spare and replacement parts for its weapons, vehicles and other equipment are counterfeit, making them vulnerable to dangerous malfunctions.” (para. 1). Last year, the GAO Congressional Counterfeit Parts report defined counterfeit material as:
- Counterfeit materiel: an item that is an unauthorized copy or substitute
that has been identified, marked, or altered by a source other than the
item’s legally authorized source and has been misrepresented to be
an authorized item of the legally authorized source. - Suspect counterfeit: materiel, items, or products in which there is an
indication by visual inspection, testing, or other information that it may
meet the definition of counterfeit materiel” (GAO-16-236 Counterfeit Parts. 2016).Awareness has significantly increased throughout the electronics industry with education and standards established by governing industry bodies such as the Institute for Printed Circuits (IPC) and the U.S. military. Even though formal programs to mitigate counterfeit infiltration such as AS5553 and IPC 1782 have been established, counterfeiters have proportionally increased packaging sophistication and techniques and their actions are nothing less than criminal. Any competent EMS provider must establish and maintain a zero tolerance counterfeit policy. Any number of potential conditions occur where EMS providers fall into the counterfeit trap including:
- Delivery demands force sourcing desperation
- Cost of requalification outweighs perceived risk of sourcing from an unlicensed distributor
- Insufficient training or lack of oversight
- Ambiguous corporate supply chain sourcing policies
- Deliberate intent to increase profit margin
- Customer supplied material with any of the previous motives
Although there are exceptions, counterfeiters tend to concentrate on specialized or hard to find integrated circuits, hybrid, or obsolete devices demanding high market value or scarcity.
Many sophisticated techniques have been developed to detect and screen through counterfeit components such as X-Ray, XRF compositional analysis, Delid/Decap Physical Analysis, various spectroscopy analyses, and electrical performance verification to unique specification parameters. Many EMS providers do not possess sufficient capital resources justifying necessary capital expenses nor does sufficient ROI exist for the investment. However, a few fundamental evaluations may detect some of the less sophisticated counterfeits attempting supply chain entrance. The following basic attributes may suggest heightened suspicion and investigation with subsequent applied analytical techniques:
1) Packaging and Labeling
Examine the packaging and labeling. Initial suspicion should occur if material is not in its original sealed and banded trays, tape and reel, or other Original Component Manufacturer (OCM) packaging. Next, review the OCM label, date code/lot code identification, part number, MSL level, logos, and environmental label. No conflict should exist between the date code or factory code printed on the devices and identifying labels. Next, examine labels for spelling errors. See Figure 1 below:

Figure 1. Environmental Handling Label Spelling Errors
2) Physical Device Characteristics
One of the most prevalent counterfeiting reidentification techniques is called “blacktopping”. This refers to using some form of abrasive, typically fine grit sandpaper, to physically remove either a silkscreen print or even laser etching identification from the component top surface, and reidentify with newer date codes, lot codes, or entirely different part numbers. For example, higher speed devices often demand a higher price and therefore are more attractive to reidentify. Examine devices under magnification and certain indicators suggest alteration as reflected in Figure 2 below:
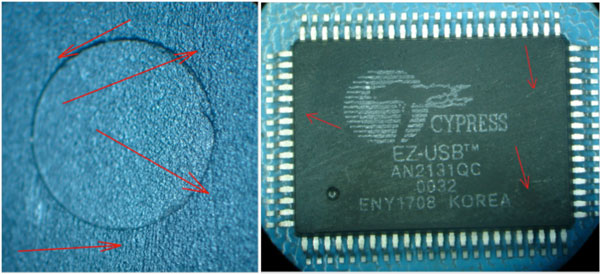
Figure 2. Sand Paper Grooves
Another blacktopping indicator is a polarity dimple texture appearance. Most polarity dimple finishes possess a shiny, texture free surface caused by either the mold injector pin surface or the encapsulation mold. Suspicion should arise if there is either no transition or signs of flaking as indicated in Figure 3 below:
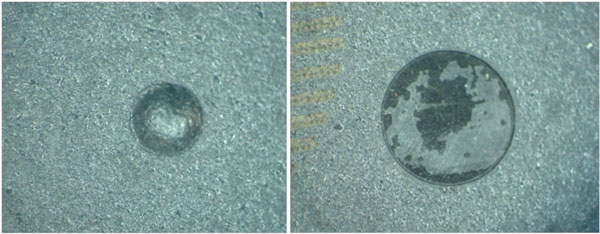
Figure 3. Blacktopping material in Polarity Dimple
The next blacktopping indicator is the surface texture transition. Integrated circuit molds may possess inherent texture variations but most molds yield a uniform top surface area and any significant dissimilarity should be regarded with suspicion. Figure 4 below reflects this condition:
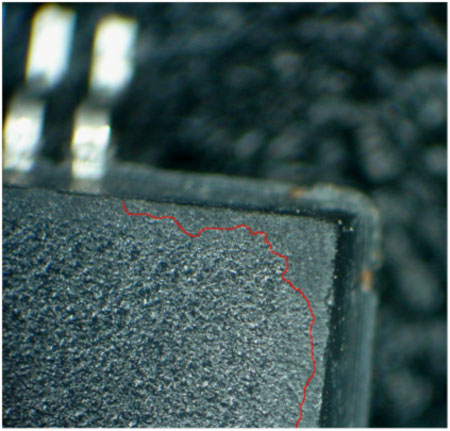
Figure 4. Blacktopping Transition
One of the most basic physical methods to determine blacktopping is applying slight forward pressure with an X-Acto knife forty-five degrees to the component surface. Blacktopping material will either flake away or roll up as a dust line along the blade edge. Depending upon thickness, this approach may take several scraping passes. After sufficient material has been removed, holding the device at different lighting angles will often reveal a ghost image of the original marking as reflected in the following Figure 5 examples:



Figure 5. Original Component Markings
In addition to blacktopping, various external mechanical characteristics should elevate concern. Reference the original component’s physical dimensions. Any micrometer measures above or below the specific thickness should cause alarm. After examining the leads under magnification, excessive corrosion, lack of coplanarity, or random surface tool marks may also suggest further investigation. In the Figure 6 example below, this counterfeit integrated circuit has two different polarity dimples for the same date code:
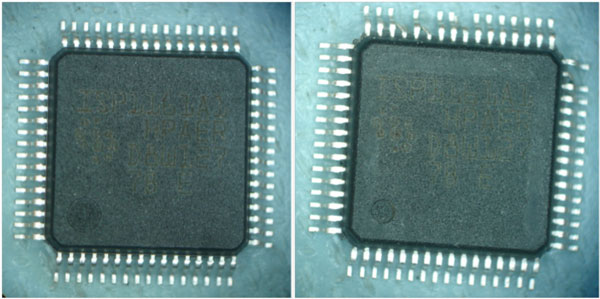
Figure 6. Two Different Polarity Dimples – Same Date Code
Selecting the quantity and location of sampling from group of suspect components must also be taken into consideration. If the components are reeled, sufficient samples must be taken from at different intervals to the innermost windings of the reel. While cumbersome, counterfeiters are aware of the perception and rely on EMS providers to evaluate only the easiest devices to access in an exterior container and will often hide altered components deep in a reel of original, unaltered components. The sample principle is true of trayed parts: take sufficient samples throughout each tray layer to ensure a proper order representation is examined. Figure 7 below represents Siemens C515 PLCC package X-Rays from a reel with all identical top nomenclature and label identification but possessed three different die variations in the same reel. These devices were all present in the same reel, interspersed throughout the reel, and the majority of counterfeits located closest to the reel hub:
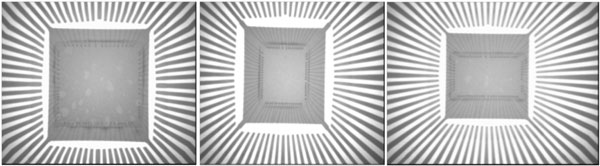
Figure 7. Same Reel Component Marking – Die Variations
EMS providers must construct sufficient safeguards to proactively prevent initial supply chain contamination in the first place. Unfortunately, customers may not always have the same necessary disciplines and therefore, a robust, dynamic counterfeit mitigation program is essential to prevent damaging consequences. The most fundamental policy an organization can require is not sourcing from unlicensed distributors or “brokers”. However, design, obsolescence, or other market conditions may force an OEM or electronic contract provider to pursue gray market sourcing. Whether an EMS provider or OEM, the foundational considerations are liability and risk. Regardless of liability, ensure that first, sufficient safeguards are in place (i.e, inspection, test, sourcing policy, training, etc.) preventing counterfeit material from entering the supply chain and, in the event discrepancies are identified downstream, a sufficient recovery plan exists eliminating any potential damage or catastrophic liability. Even the most authentic appearing pedigreed OCM certificates of conformance are forged to project legitimacy.
Preventing, detecting, and eliminating counterfeit material is a social and industry conscientious responsibility. All stakeholders are responsible for alerting customers, distributors, and customers through the Government–Industry Data Exchange Program (GIDEP), specific customer protocols, or whatever available means to contain current identified counterfeit material, prevent its current use, and ensure that the material is removed and destroyed from the current supply chain. According to Bloomberg author Sandra Erwin “The Pentagon is taking steps such as increasing cybersecurity training for procurement officials and is trying to raise awareness of the risks, but the overwhelming responsibility for preventing and catching bad actors falls on contractors, simply because they are the first line of defense.” (2016, para. 7).
The fraudulent electronics threat has been recognized for decades and even with the additional focus and standardization to detect and eliminate counterfeit electronics from the industry, it remains the responsibility of every EMS provider, OEMs, distributors, and stakeholders to prevent counterfeit material from entering the supply chain in the first place, maintain capability to identify, and properly disposition to prevent any current or future use. Like Electrical Overstress Events (EOS) due to poor ESD practices, failure doesn’t necessarily occur at the moment of power application. Recycled components may have already experienced environmental, mechanical, or electrical conditions causing failure not manifesting until multiple power up cycles at a week, a month, or even years. In reality, detecting and eliminating counterfeit electronics from your supply chain involves relatively inexpensive initial resources yet yields exponential dividends to your organization and your customer.
Reference:
Erwin, S.I. (October 2016). Pentagon Pleads with Contractors to Step Up Fight Against Industrial Espionage. Para. 7. Retrieved from https://about.bgov.com/blog/pentagon-pleads-contractors-step-fight-industrial-espionage/
GAO (February 2016). “COUNTERFEIT PARTS”. GAO-16-236. p. 7.
Greenemeier, L. (April 2017). “The Pentagon’s Seek-and-Destroy Mission for Counterfeit Electronics.”
Scientific American. Retrieved from https://www.scientificamerican.com/article/the-pentagon-rsquo-s-seek-and-destroy-mission-for-counterfeit-electronics/
Philip P. Thurman
Phil is currently the Quality Assurance Director for Quality Manufacturing Services, Inc. and has been a manufacturing quality assurance executive for 30 years with extensive experience in military power management systems, electronic manufacturing services, and quality systems applications. Receiving a BA in English from Stetson University and an MBA in Organizational Leadership from Norwich University, he is a published author and often consulted for electronic systems manufacturing development guidance. His extensive knowledge offers unique insights into industry trends, manufacturing advancements, and the continuing role of quality assurance evolution relative to technological progression.

